Malware Families Attempting to Exploit Legacy Vulnerability (CVE-2017–11882) | by Venus Chhantel | Medium

Malware Families Attempting to Exploit Legacy Vulnerability (CVE-2017–11882) | by Venus Chhantel | Medium

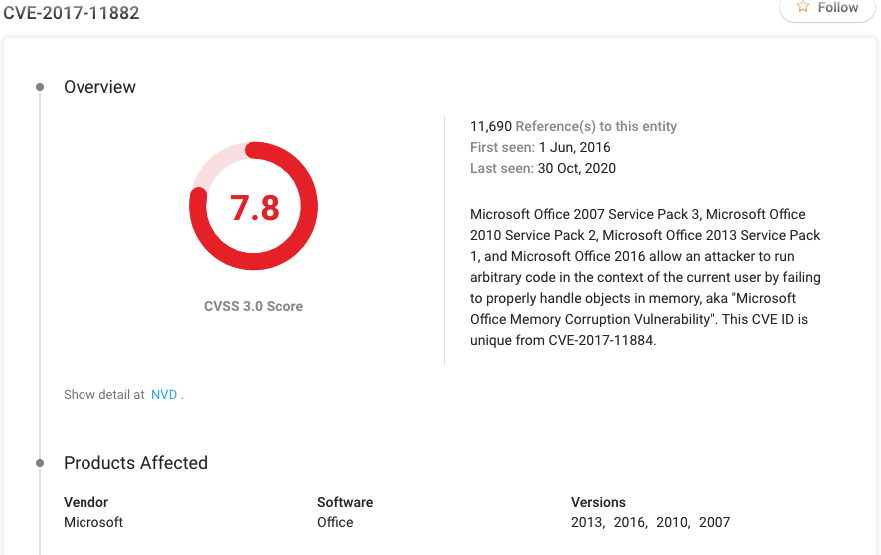
CVE-2017–11882 is a distinct Common Vulnerabilities and Exposures (CVE) entry, denoting a security… | by ASM Cybersecurity | Oct, 2023 | Medium

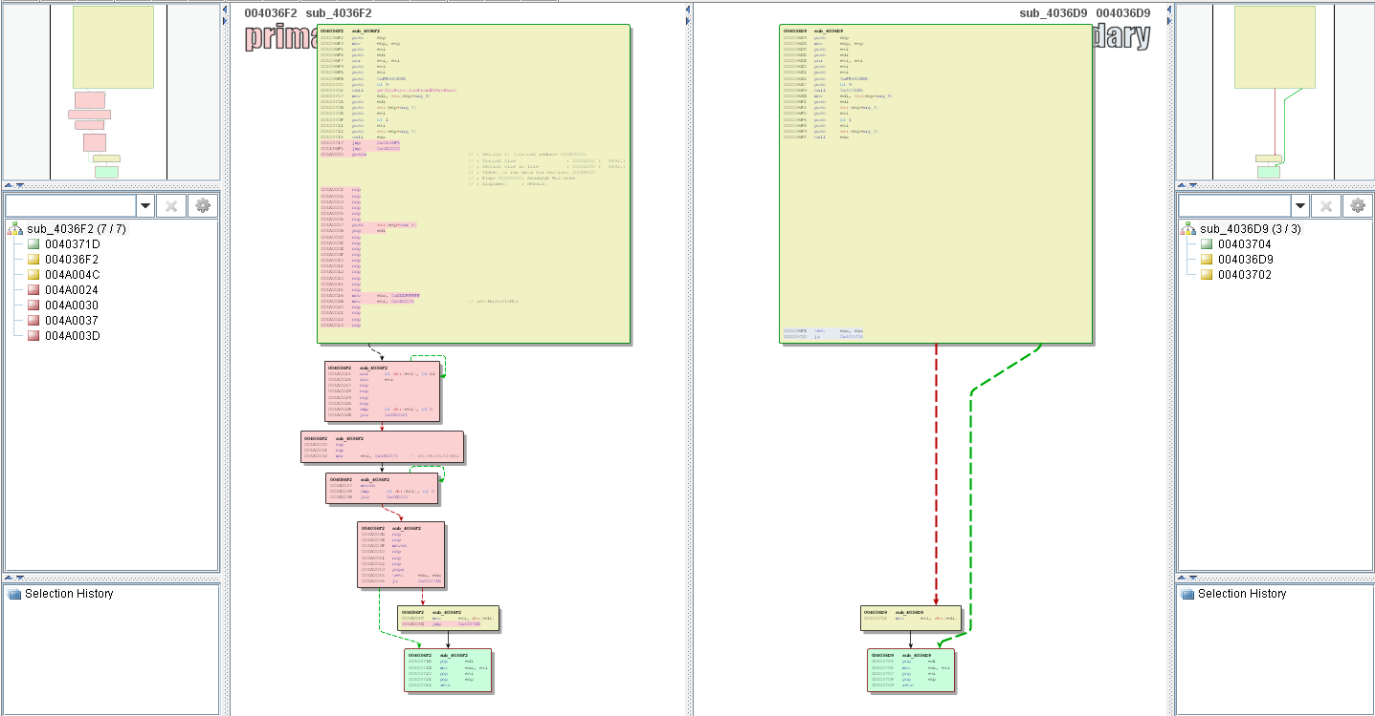
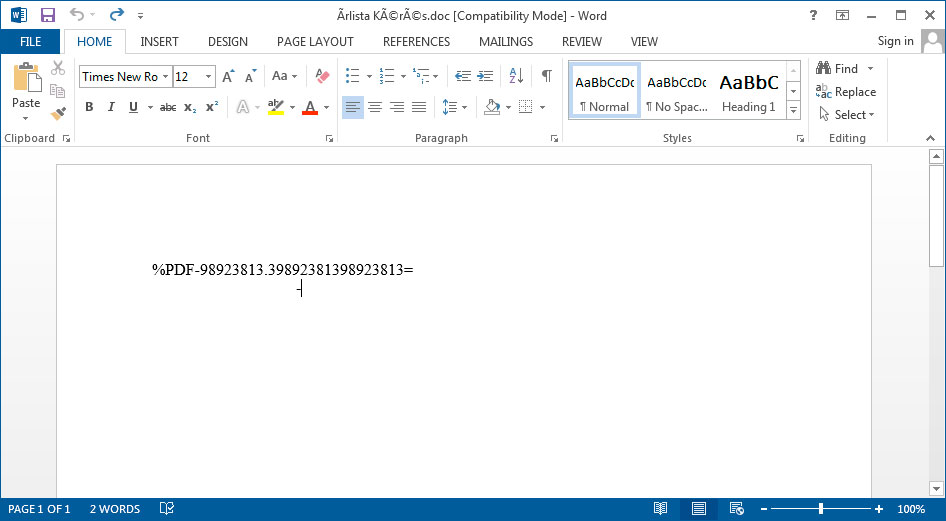
17-Year-Old MS Office flaw CVE-2017-11882 could be exploited to remotely install malware without victim interaction

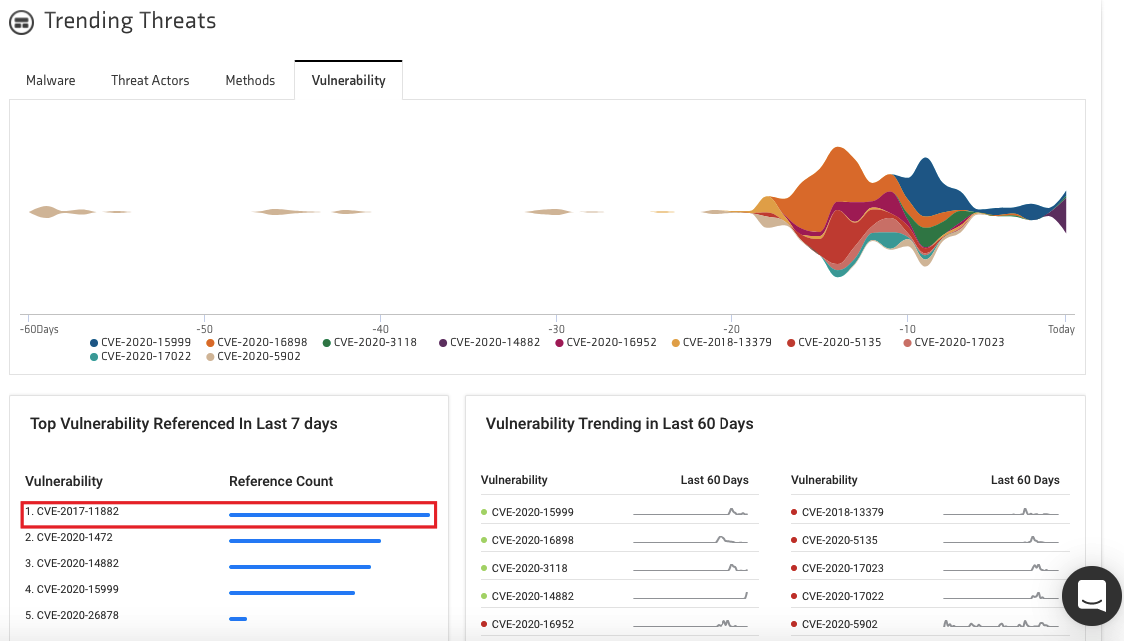
CVE-2017-11882: Two-Decades-Old Vulnerability in Microsoft Office Still Actively Leveraged For Malware Delivery - SOC Prime